Applies to Version 1.10 or higher
Introduction
The Identity Architecture below provides an overview of the Identity connections between the various components of the IBSS Solution and the 3rd Party Identity Provider (IDP).
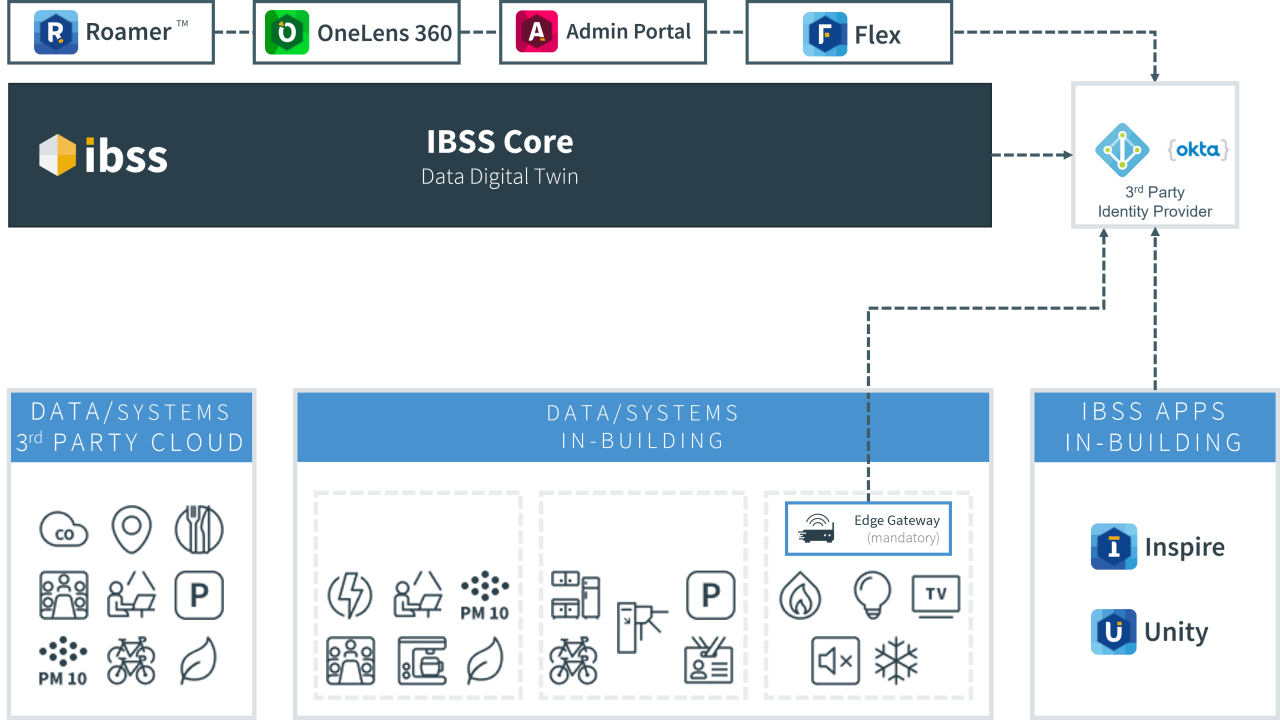
Identity Connections
A typical IBSS deployment has four types of connections to the Identity Provider
- IBSS Core – Data Digital Twin: will synchronise the users and groups that have access rights to the solution
- IBSS In-Building Apps: Will validate their logon credentials against the Identity Provider
- On-Premises Data Systems: If there is an Edge Gateway device providing control functions for the In-Building IBSS Apps, it will synchronise the users and groups that access rights to the local control points
- IBSS User Apps: Will validate their logon credentials against the Identity Provider
The IBSS Solution is designed to make use of a 3rd Party Identity Provider to cleanly integrate with the corporate infrastructure. IBSS currently supports the following 3rd Party Identity Providers:
- Azure Active Directory
- Azure Active Directory B2C
- Okta
Azure Active Directory
The IBSS Solution uses the following capabilities from Azure Active Directory:
- Users and Roles synchronisation
- Login validation
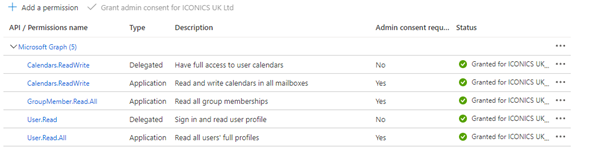
Graph API Permissions
The following are the required Graph API permissions for the IBSS platform to operate
Permission |
Why it's needed |
Where |
|---|---|---|
User.Read.All |
Sync users from AAD to IBSS. |
Cloud Services |
GroupMember.Read.All |
Sync groups from AAD to IBSS. |
Cloud Services |
User.Read |
Allow the user to sign in via AAD. |
Client Apps |
Calendars.ReadWrite (Delegated) |
Allow the app to add calendar entries to the user's calendar. |
Client Apps |
Calendars.ReadWrite (Application) |
Allow the back-end to sync to meeting room calendars and to manage calendar entries for auto-cancellations. |
Cloud Services |
Okta
The IBSS solution supports connection via OpenID Connect (OIDC) to Okta. The IBSS Solution uses the following capabilities from Okta:
- Users and Roles synchronisation
- Login validation
Constraints
Both Azure Active Directory & Okta support guest accounts (i.e. accounts that have a different email domain than the 'normal' users) within the scope of their identity provision, however for this to work within IBSS the following constraints must be met
- the email address used must be a standard email address
- the unique name must only contain alphanumeric (a-zA-Z0-9), period/full-stop (.) and the single @ sign
- every email address can only be used once, so if multiple identity providers are used, ensure that a normal account in one Identity Provider is not the guest account in another Identity Provider.